What is Cybersecurity?
Cybersecurity is the technique of protecting critical systems, networks, and programs from digital attacks and aggression.
table of contents:
- What is cybersecurity
- Why is cybersecurity Important?
- cybersecurity challenges
- cybersecurity threats
- Types of CyberSecurity
- cyber security technologies
- Cyber security trends 2022
- Cyber Security Frameworks
- cybersecurity career
- Security is everything
These cyberattacks usually aim to access, change, or destroy sensitive data and information, extort money from users, or interrupt typical business functions.
Executing effective cybersecurity measures is incredibly challenging today because there are more devices than people, and attackers are becoming more ingenious.
about personally identifiable information (PII)
Cybercriminals target customers’ personally identifiable information (PII) ( names, addresses, national identification numbers, and credit card information ) and then trade these records in underground digital marketplaces. Compromised PII often leads to a loss of customer trust, the imposition of regulatory damages, and even legal action.
But organizations with a comprehensive cybersecurity strategy handled with the best techniques and automated using advanced analytics, machine learning, and artificial intelligence (AI), can fight cyber threats more effectively and lower the lifecycle and impact of breaches when they occur.
Why is cybersecurity Important?
Currently, there is a large and pronounced increase in the number of users, programs, and devices in the current enterprise and institutions, in addition to the data that are considered confidential and sensitive, all of which leads us to an increased interest in cybersecurity.
The growing volume and sophistication of cyber attackers and attack practices compound the problem even further
What are the top cybersecurity challenges?

- One of the most common cybersecurity problematic elements is the evolving nature of security risks.
With the emergence of more advanced technologies and the use of technology in new or different ways, new methods of attack are invented.
Sometimes keeping pace with these frequent changes and developments in attacks, as well as updating and developing practices to protect against them, can be difficult.
Challenges include ensuring that all elements of cybersecurity are constantly updated to protect against vulnerabilities and threats.
But this is sometimes difficult for smaller organizations
- Another challenge to cybersecurity includes a shortage of skillful cybersecurity personnel.
As the amount of data collected and used by interactions grows, the need for cybersecurity teams to analyze, manage and respond to incidents also increases.
The International Information Systems Security Certification Consortium (ISC)2
(ISC)2 estimated the workplace gap between needed cybersecurity positions and security experts at 3.1 million positions.
Common And Types of cybersecurity threats
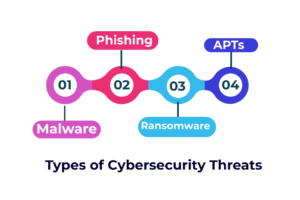
Types of cybersecurity threats
Malware
malware is a type of malicious software such as viruses, worms, and spyware created to provide unauthorized access or to cause damage to a computer.
Phishing / social engineering
phishing is a practice of tricking users to provide their own PII or sensitive data and information, In phishing scams, they send emails or text messages from unreliable sources but they appear to be from a legitimate company asking for sensitive and private information such as national identification numbers, and credit card information or login information.
you can help yourself that you must never send any sensitive information without making sure that you send it to the right place, not others
and or you can educate yourself on a technology solution that filters malicious emails
Ransomware
Ransomware is a type of malicious malware it is created and designed to extort money and lock down or block access to files and destroy the data Threatening to make private or sensitive data to the public unless a ransom is paid to the cybercriminals who designed and launched this malicious attack
However, Paying the ransom does not warrant that the files will be recovered or the system restored
Advanced persistent threats (APTs)
(APT) is a prolonged and targeted cyberattack
which is A group of intruders infiltrate a system and remain hidden for a long period
APT attacks originated to steal information and sensitive data rather than cause harm to the target organization’s network.
Basically, The intruder doesn’t do any harm to networks and systems and leaves them intact so that he can spy on activities and steal sensitive data while avoiding the activation of any defensive countermeasure.
Types of CyberSecurity
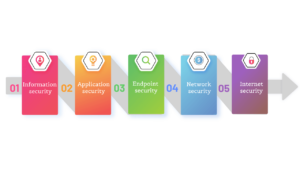
Types of CyberSecurity
- firstly: Information security
- secondly: Application security
- thirdly: Endpoint security
- fourthly: Network security
- fifthly: Internet security
Information security
Information security applies to an organization’s data using confidentiality, integrity, and availability ( CIA Triad ) principles.
Organizations use a wide range of tools and policies to maintain information security through technical measures that protect data internally with security measures that protect the location in which the data is stored
Application security
software tools that businesses use various programs to complete daily tasks and publish all updates.
The developers who use these applications are responsible for monitoring and addressing any security vulnerabilities and carrying out security tests and application protection products
These tools help in finding weaknesses and creating defensive measures against any threats
Endpoint security
Endpoints pose a major threat to cybersecurity because monitoring them effectively may need to disrupt production, so it is difficult to monitor them without disrupting productivity.
Endpoint security applies to any end-user device connected to the corporate network, including smartphones, laptops, desktop computers, tablets, and IoT devices
Network security
Network security applies to the hardware and software used to prevent the access of any unauthorized devices or applications.
also, tools include vulnerability scanning applications, identity management software, virtual private networks, and user behavior analysis tools.
includes three important stages:
Security: Refers to configuring network settings in addition to the settings of each device or application on the network.
Detection: Detection refers to the continuous monitoring of any activity on the network to identify anomalies and patterns
Response: the actions and reactions of the mechanism to treat potential problems
Internet security
Cybersecurity threats often come from Internet activities that are accessed over the Internet and devices that use the Internet to complete tasks. Internet safety tools include password chiefs, firewalls, and antivirus software.
List of cyber security technologies :
- Artificial Intelligence & Machine Learning
- Application Security
- Web security
- Social engineering or insider threat
- Internet of Things
- Blockchain
- Cloud computing
- Firewalls
- Intrusion Detection System (IDS) and Intrusion Prevention System (IPS)
- Data Loss Prevention (DLP) & Data encryption
Cyber security Trends 2022
- Attacks Against Cloud Services
- Rise in IoT Devices
- Integration of AI & Machine Learning
- Zero Trust Cyber Security
- Privacy Enhancing Computation
- Multi-Factor Authentication
- Continuously Evolving Ransomware
- A rise in Insider Threats
- An explosion of BYOD & Mobile Devices
- Growing IT Skills Gap
- Increasing Threat of Deepfakes
- A rise in Political Cyber Warfare
- Organizational Behavior
- Connected Cars
What Are the Types of Cyber Security Frameworks?

1. Control Frameworks
develops a basic strategy to help reduce security risk.
improve the efficiency of an organization’s operations and provides a group of security controls
Prioritizes implementation of the organization’s cyber security pillars and helps to execution of security controls
2. Program Frameworks
A program framework designed to focus on and assesses the state of the organization’s security program and measure the competitive analysis
evaluate and Constructs a cybersecurity program
Additionally, simplifies the communications channel between the cyber security team and the organization’s management
3. Risk Frameworks
identify and Defines the necessary processes for risk management
the risk framework Structures a security program for helps safeguard the system
measures the organization’s security risks
CyberSecurity Framework Best Practices
In totality, there are five elements to the Cyber Security Framework:
- First: Identity
- Second: Protect
- Third: Detect
- Fourth: Respond
- Fifth: Recover
cybersecurity career
Cyber security is a fast-growing field in the fields of information technology concerned with the risks of hack, extortion, and theft of accurate and sensitive data and information… Therefore, this field requires that you possess a sufficient amount of experience and professionalism.
According to the organization’s strategy statistics, it was found that 46% of companies and organizations have a problematic lack of cybersecurity skills.
As of 2015, the deficit was up to 28%, which means that the need for this field is increasing, as organizations and commercial, governmental, and private companies all use cybersecurity specialists
Become a member of our team today
Interested? Apply now
cybersecurity job titles include:
- Security Engineer
- Security Administrator
- Chief Information Security Officer (CISO)
- Security analyst
- Chief Security Officer (CSO)
- Security Architect
- Data Protection Officer (DPO)
- Security Consultant/Specialist/Intelligence
Security is everything
– When it comes to digital transformation and security, it is a development that doesn’t stop, and every day there is technological development. generally, Organizations must think about the provisions of security and safety.
accordingly, Security requires that you be proactive about creating a protected environment, which means the presence of periodic instructions and comprehensive training regarding all security rules.
- Cybersecurity frameworks help teams address cybersecurity challenges, providing a strategic, well-thought technique to protect their data, infrastructure, and information systems. basically, The frameworks offer guidance, allowing IT security leaders to manage their organization’s cyber risks more intelligently.
- Organizations can acclimate and adjust a current framework to satisfy their requirements or create one internally. However, the latter option could pose challenges since some enterprises must adopt protection frameworks that comply with commercial or government regulations. Home-grown frameworks may verify insufficient to meet those standards.
- Generally Frameworks help organizations follow the correct safety procedures, which not only supports the organization’s safe but fosters consumer confidence. overall Consumers have fewer reservations about doing business online with institutions that follow established security protocols, keeping their financial data safe.